The True Cost Of A Data Breach To Small Business Explained
Rich Selvidge on July 18, 2024

While the true cost of a data breach varies the average small business can expect to pay $120,000 to $1.24M to respond and resolve the issue.
These costs may include:
- Direct financial damages.
- Employee hours spent resolving the breach.
- Hiring firms specializing in incident response.
- Loss of revenue from clients.
- Higher insurance premiums.
- Penalties for non-compliance.
Extended Threat
Protection (XTP)
Monthly subscription
(per device)
*All prices listed are in US Dollars. Subscription will automatically renew for 1 month from the date of purchase unless you cancel.
Helios Cloud™
Enterprise Security
Monthly subscription
(per device)
*All prices listed are in US Dollars. Subscription will automatically renew for 1 month from the date of purchase unless you cancel.
There is also the human factor of IT and security teams working long hours under considerable stress to respond to the threat and restore network operations.
In this article, we’ll look at what’s driving these attacks and more importantly how you can protect yourself from becoming another statistic.

The Rise Of Cyber Attacks On Small Business
Small businesses and startups are focused on two things:
- Developing their product/service offerings.
- Growing their business.
Often, cybersecurity is an afterthought, unless external factors, such as compliance requirements, push for adequate security controls to be in place.
According to Verizon’s 2023 Data Breach Report, ransomware attacks remain the number one contributor to data breaches with financial gain being the primary motive.
- Ransomware attacks more than doubled between 2022 and 2023, rising from 25% of all data breaches to 62% in 2023.
- Business email compromise has almost doubled and represents more than 50% of incidents.
Social engineering continues to be an effective and lucrative entry point for attackers, specifically when combining vishing and phishing techniques.

The Financial Impact Of Data Breaches
Direct financial damages
When a data breach hits, it’s like a punch to the gut for any business, hitting you right where it hurts: your finances.
According to Sophos’s 2023 State of Ransomware Report, the average cost of a ransomware demand is $1.54M, almost double from the $812,380 average in 2022.
Suddenly, you’re at a crossroads.
- Do you pay the ransom and get back to business as usual?
- Or brace yourself for the fallout, which could mean anything from your systems being down for days, losing critical data, or damaging your reputation.
Learn More: 10 Ways To Protect Your Small Business From Ransomware
In the case of Mission Community Hospital, a ransomware attack in May 2023 had severe repercussions.
Unauthorized access to their network was discovered enabling the RansomHouse ransomware group, who claimed responsibility for the attack, access to files containing sensitive patient data, including:
- Names
- Addresses
- Social Security numbers
- Health information
As a result, hospital operations were disrupted, forcing them to implement additional security measures and offer affected individuals a year of credit monitoring and identity theft protection.
While the loss of revenue may seem necessary to get back to business, it marks the business as an easy target for future attacks.
It isn’t just a one-time financial hit. It’s a decision that can lead to ongoing financial exploitation.
It signals to cybercriminals that you are a target who might pay up again, increasing your risk of repeated attacks and escalating demands.
These repeated attacks can lead to a financial strain that might be too much for the business to bear, risking its closure.
Employee hours
The financial implications of a ransomware attack go beyond the direct financial implications, particularly concerning employee hours spent resolving the issue.
Time is spent in meetings planning, developing the organization’s strategy, and then executing on that plan.
This is time and money that would have otherwise been used to work on more impactful projects to grow and expand the business.
Executive Meetings
High-level strategy sessions with executive team members is a requirement and may include the CEO, CFO, CIO, CISO, CLO, and CMO.
These meetings often involve discussions about the:
- Financial implications.
- Incident response planning and triage.
- Negotiation strategies with the attackers.
- Preparing communications to stakeholders and clients.
- Long-term business impact of the attack.
Given the seniority of the participants, the cost per hour for these meetings can be quite high, reflecting the significant salaries and opportunity costs involved.
The seniority of these participants drives the cost higher, potentially reaching $500 to $1,000 per hour for each executive.
To put this into context, for a 1-hour executive meeting with 6 executives, the total cost could range from $3.000 to $5.000 per meeting. If these meetings are held twice a week in response to the crisis, the cost could be between $6,000 and $10,000.
Internal/External IT And Security Team Meetings
This typically includes the internal IT team, cybersecurity personnel, and possibly members of the network and system administration teams.
Given the technical expertise required, the hourly rate for IT and cybersecurity team members can range from $75 to $150. This rate accounts for their specialized skills and the urgency of the situation.
Assuming a 2-hour long meeting with an 8-member team, the cost per meeting could range from $1,200 to $2,400. If these meetings occur once a day during the critical first week of a ransomware response, the total weekly cost would be between $6,000 and $12,000.
If you do not have internal resources these costs could easily double as contractor hours are always more expensive over internal resources.
Outsourcing Incident Response
Outsourcing incident response to specialized security vendors is a common due to lack of internal expertise, however, it is an expensive choice in ransomware situations.
The cost of an Incident Response Retainer (IRR) varies significantly across vendors, ranging from $800 to $1000 per hour for some, while others might charge between $300 to $500 per hour.
The total cost could exceed $100,000 depending on the extend of the breach.
This price disparity reflects the diverse range of services, from bespoke security solutions to broader cybersecurity consulting offerings.
PR And Communications Meetings
These meetings involve PR teams, communications specialists, and possibly external PR agencies.
The focus is on developing communication strategies for stakeholders, including customers, employees, and the media, to manage the company’s reputation and address concerns.
The cost of these meetings adds up, particularly if external consultants or crisis communication experts are involved.
Each participant may cost between $150 to $300 per hour.
For a 2-hour meeting with 6 participants, the total cost can range from $1,800 to $3,600 per meeting. If these meetings occur three times a week for ongoing crisis communication, the total cost per week could range from $5,400 to $10,800.
Non-compliance
HIPAA Violations
As of October 6, 2023, the penalties for a HIPAA violation are categorized into four tiers based on the level of culpability:
- Tier 1 (Reasonable Efforts): Minimum of $137 to a maximum of $68,928 per violation, with an annual limit of $2,067,813.
- Tier 2 (Lack of Oversight): $1,379 to $68,928 per violation, capped annually at $2,067,813.
- Tier 3 (Neglect – Rectified within 30 days): $13,785 to $68,928 per violation, with the same annual limit.
- Tier 4 (Neglect – Not Rectified within 30 days): Each violation costs $68,928, with an annual maximum of $2,067,813.
Annual penalty limits for tiers 1 to 3 have been reduced following a reexamination of the HITECH Act, with caps set at $25,000 for tier 1, $100,000 for tier 2, and $250,000 for tier 3, subject to inflation.
The maximum for tier 4 remains at $1,500,000.
PCI DSS Violations
Penalties for non-compliance with PCI DSS as of 2023 are structured based on the duration of non-compliance:
- For the first three months: Fines range from $5,000 to $10,000 per month.
- For months four to six: Penalties increase to $25,000 to $50,000 per month.
- Beyond the seventh month: Charges escalate to $50,000 to $100,000 per month.
GDPR Violations
The European Union’s General Data Protection Regulation imposes stringent data protection standards, with significant penalties for non-compliance broken down into two categories:
- Minimum Fines: Entities that fail to comply with GDPR regulations can face fines of up to €10 million or 2% of the company’s worldwide annual revenue from the preceding financial year, whichever is higher. This applies to less severe infringements such as having improper records or failing to notify about breaches.
- Maximum Fines: For more serious offenses, the fines escalate to a maximum of €20 million or 4% of the company’s annual global turnover, again choosing whichever amount is higher. This represents the upper limit of financial penalties under GDPR for non-compliance.
CCPA Violations
The CCPA imposes significant fines for non-compliance, specifically for companies operating in California or serving Californian customers.
- Civil Violations: Non-compliance can attract a maximum fine of $2,500 per violation. This applies to general breaches of the privacy legislation.
- Intentional Violations: More severe penalties are in place for intentional violations, with fines rising to $7,500 per incident.
- Legal Actions: In addition to these fines, companies non-compliant with the CCPA also face the risk of legal action initiated by customers themselves, adding another layer of potential financial burden.
Insurance
In the past, insurance companies underwrote cybersecurity policies without fully understanding the complexities and implications of security requirements.
Today’s cybersecurity insurance policies mandate stringent due diligence and specific security controls as prerequisites for coverage.
Stringent Requirements For Policy Compliance
Proof Of Implemented Security Measures: Insurance providers now require companies to demonstrate that they had reasonable and effective security measures in place at the time of a data breach. This involves documenting and proving adherence to various security protocols and practices that align with the policy’s requirements.
Liability In Absence Of Adequate Security: If a company fails to implement the necessary security measures, insurance providers may use this as grounds to deny claims or minimize payouts. This places a financial burden on businesses, as they are left to handle the fallout of a data breach without adequate financial support.
Impact On Insurance Premiums
Increased Premiums Post-Breach: Following a data breach, businesses often face a significant increase in their cybersecurity insurance premiums. This is due to the elevated risk profile associated with a history of security incidents. Higher premiums translate into increased operational costs, directly affecting a company’s bottom line.
Cost Of Enhanced Coverage: As cybersecurity threats evolve, businesses may find themselves needing more comprehensive insurance coverage, which comes at a higher cost. Balancing the need for adequate coverage against the expense becomes a critical financial decision.

The Indirect Costs Of A Data Breach
Reputation
From Existing Customers
Erosion Of Customer Trust: A data breach often leads to a loss of trust among existing customers. Trust is important for customer loyalty and retention. When customers feel their personal information is no longer safe with a company, they are likely to discontinue their business relationships.
Increased Customer Churn: The immediate aftermath of a data breach typically sees an increase in customer churn rates. Customers concerned about their privacy and security are more inclined to switch to competitors, thereby reducing the company’s recurring revenue.
Cost Of Remediation And Compensation: Post-breach, organizations often find themselves spending significantly on remediation efforts, including compensations offered to affected customers. This might include free credit monitoring services, refunds, or other forms of compensation that directly impact the revenue.
From Future Business Opportunities
Damaged Brand Reputation: The long-term impact of a data breach on a company’s brand reputation can be profound. A tarnished reputation can deter potential new customers, affecting future revenue growth.
Impact On Business Partnerships And Deals: A breach can also lead to a loss of potential business deals and partnerships. Other businesses might view the breached organization as a liability, impacting collaborations, mergers, acquisitions, or other business opportunities.
Loss of Competitive Advantage: In highly competitive markets, a breach can cause a significant setback, allowing competitors to capture market share while the affected company is still recovering. This loss of competitive edge translates into lost potential revenue.
Stolen Intellectual Property
Imagine seeing years of your team’s innovative work, those secret recipes that set your business apart, just vanish or, worse, turn up in a competitor’s hands.
That’s what happens with IP theft during a data breach.
It’s not just about the immediate loss; it’s the future ideas, products, and unique services that could have defined your market presence, all gone in a blink.
You may also lose your competitive edge in the market if this IP falls into the wrong hands.
Future investments Opportunities
In the business world, confidence is king. A data breach can shake that confidence, making investors think twice.
They’re looking for stability and security, and a breach raises red flags; especially in sensitive or highly targeted markets.
It’s not just about the now; it’s the lost potential, the deals that don’t close, and the expansion plans that get shelved because investors are wary.
Impact on employees
Think about the people behind the scenes when a breach hits – your IT and security teams. They’re suddenly in the eye of a storm, racing against time, under immense pressure to fix things.
Attackers will often wait to execute their campaigns around the holidays, which is when your teams need to be resting the most.
It’s a heavy load to carry, often leading to long hours and stress that can burn out even your most dedicated employees.
Your team members may start questioning their own capabilities and wrestling with stress and uncertainty. It’s tough, and sometimes, it’s too much.
This emotional toll can lead to good people leaving, looking for calmer waters. And each time someone walks out that door, they take a piece of your business’s internal expertise with them, along with years of experience that isn’t easy or cheap to replace.
The Challenges Of Implementing Security For Small Businesses
In my experience in speaking with hundreds of CXOs, founders, and IT leaders over the past 5 years, I can tell you that many take a backward approach to security.
They are often pushed by compliance, insurance, investors, or client requirements to implement some sort of security measures.
Unfortunately, this leads to what I call, “checkbox security,” or security for the sake of meeting business objectives. While the goals of the company should lead security decisions, it shouldn’t take priority in all things.
For example, many small businesses will receive a 300 point questionnaire leading to implementing security policies.
Great, you’ve implemented the policies but are you doing what you say you’re going to do?
Further, penetration testing services are sought out to identify vulnerabilities and attack paths that a threat actor might take.
But what’s the point of testing the locks on your door if you don’t have a door?
Without a proper cybersecurity program in place, these initiatives only provide the guise of security.
So what do you do if you want to maximize the return on your security investments (ROSI) while meeting business objectives?
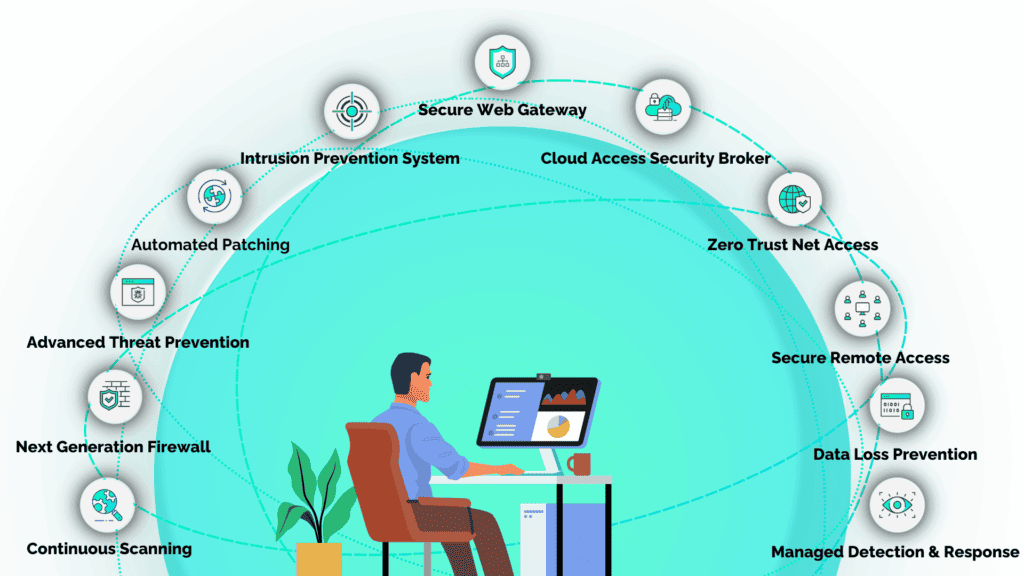
How SecureTrust Protects Small Businesses From Data Breaches
SecureTrust addresses these security challenges head-on with its innovative solutions tailored for small businesses.
Our team comprises experts trained by the Department of Defense, equipped with the skills to monitor, detect, respond, and proactively hunt threats.
We ensure that small businesses remain compliant with the latest standards and best practices in cybersecurity.
Our fully managed service model is subscription-based, making it an affordable, scalable, and flexible solution for small businesses. It’s easily accessible through the cloud and customizable to fit diverse business needs.
With SecureTrust, small businesses can confidently navigate the complex landscape of cybersecurity, ensuring their data and operations are safeguarded against the evolving threat of cyber attacks.
Our approach integrates several key elements:
Secure Access Service Edge (SASE)
We employ SASE delivered through Helios Cloud™ to provide comprehensive network security, combining wide-ranging network security functions with wide-area networking capabilities.
These holistic security features include:
Microsegmentation
Our solution leverages microsegmentation to break down networks into smaller, more manageable zones, each with specific security protocols.
This strategy not only prevents the spread of threats at a user and device level but also offers more granular control over security policies.
3 Factor Authentication (3FA)
To prevent 99.9% of password compromises SecureTrust uses a robust 3 factor authentication system.
3 factors of authentication include:
- Something you know (username/password)
- Something you have (hardware token)
- Something you are (biometric such as a fingerprint).
These are low cost high impact security measures you can take.
Learn More: What Is 3 Factor Authentication?
Continuous Vulnerability Management
Vulnerabilities are released and disclosed daily meaning your organization must adopt a continuous scanning and patching cycle.
Recent research suggests that on average vulnerabilities are not discovered for up to 6 months.
Further, critical and high vulnerabilities on average are remediated 60 to 150 days after they’ve been discovered.
These vulnerabilities are an entry point that threat actors use to deploy malware on systems to conduct ransomware attacks. Is this a risk you’re willing to accept?
- Category: Small Business











