How Ransomware Spreads In 2024: 5 Common Methods
Rich Selvidge on January 5, 2024

The most common methods used by threat actors to spread ransomware in 2024 are:
- Social Engineering
- Unpatched Systems
- Bypassing Multi Factor Authentication
- Supply Chain Compromise
- Infected USB Drives
In this article, we’ll discuss the impact ransomware has on businesses and explain exactly how these attacks spread.
We’ll also provide practical steps you can take to protect yourself and your business from these rising threats.
Extended Threat
Protection (XTP)
Monthly subscription
(per device)
*All prices listed are in US Dollars. Subscription will automatically renew for 1 month from the date of purchase unless you cancel.
Helios Cloud™
Enterprise Security
Monthly subscription
(per device)
*All prices listed are in US Dollars. Subscription will automatically renew for 1 month from the date of purchase unless you cancel.

The Cost Of Ransomware Rises In 2024
Ransomware continues to be the number 1 threat to businesses of all sizes worldwide.
The cost of a data breach for small businesses averages $120,000 to $1.24M, and the total average cost worldwide reached an all time high of $4.45M in 2023, with the average ransomware demand coming in at $1.54M.
These costs can be direct and/or indirect, adding $100,000s in recovery costs:
- Paying the ransom.
- Direct financial damages.
- Employee hours spent resolving the breach.
- Hiring firms specializing in incident response.
- Loss of revenue from clients.
- Higher insurance premiums.
- Penalties for non-compliance.
Small and medium sized businesses are a frequent target for ransomware groups, which saw a 47% rise in attacks in the first half of 2023.

What Are The Most Common Ways Ransomware Spreads?
1. Social Engineering
According to Verizon’s 2023 Data Breach report, 74% of all breaches begin with a social engineering attack.
The Cybersecurity & Security Infrastructure Agency (CISA) defines social engineering as:
In a social engineering attack, an attacker uses human interaction (social skills) to obtain or compromise information about an organization or its computer systems.
Common online techniques include email phishing and vishing.
When used independently these tactics have a success rate between 30%-37%. However, when used together in a coordinated campaign, the success rate increases to around 75%.
In the case of Caesars Entertainment, they suffered a social engineering attack targeting their outsourced IT support vendor.
Scattered Spider, the ransomware gang claiming responsibility for the attack, allegedly downloaded the personally identifiable information (PII) of more than 65M members of Caesars’ loyalty program.
In addition, over 41,000 Maine residents’ data was exfiltrated.
Unfortunately, Caesars chose to pay the ransom for the sum of $15M.
The FBI recommends that you NEVER pay the ransom as only 8% of victims manage to get back all of their data after paying.
Despite this, a survey of 350 CISOs found that more than 4 in 5 CISOs said their organization paid the ransom.
2. Unpatched Systems
Threat actors are searching for the lowest hanging fruit to maximize their revenue. Systems that have known exploitable vulnerabilities are exactly what they’re looking for.
Recent studies show 60% of breaches involve vulnerabilities for which a patch was available but not applied.
The time to identify a new vulnerability averages around 6 months, and remediation of critical or high vulnerabilities can take between 60 to 150 days.
Traditional patching cadences, such as monthly or weekly, are inadequate at addressing the countless new vulnerabilities disclosed every day.
With the proliferation of automation and now AI, the entire process of encrypting an organization takes under 45 minutes, with a median time of just under 6 minutes.
Instead, businesses should adopt a continuous vulnerability management program where systems are scanned and patched daily for vulnerabilities.
This significantly reduces the risk to an organization by shortening the time a known exploitable vulnerability sits on your network.

3. Bypassing Multi Factor Authentication
61% of all breaches have exploited user credentials, with half of these incidents directly attributed to stolen credentials.
Multi factor authentication (MFA), particularly 2 factor authentication (2FA), is widely regarded as a robust security measure.
However, text and voice authentication methods can be easily bypassed, often by leveraging basic phishing emails to gain account credentials.
Research has also shown how adversarial AI can manipulate audio authentication, a technique often used in voice-based 2FA.
In one case, a reporter was able to break into a bank account using AI generated voice offered by a free voice creation service from ElevenLabs.
Application based authentication is also vulnerable, despite Microsoft’s claim that it can prevent 99.9% of account take overs.
Okta, a major identity management company, experienced a data breach impacting all customer support users.
Initially, Okta had reported that only around 1% of its customers, or 134 organizations, were affected.
It was later confirmed that the breach impacted all Okta customers, which numbered around 18,000, including prominent companies like:
- 1Password
- Cloudflare
- OpenAI
- T-Mobile
- MGM Grande
4. Supply Chain Compromise
Supply chain compromise involves infiltrating a trusted software provider or vendor to distribute ransomware.
For the first time in 2022, supply chain attacks surpassed the number of malware-based attacks by 40%.
More than 10 million people were impacted by supply chain attacks targeting 1,743 entities. By comparison, 70 malware-based cyberattacks affected 4.3 million people.
By compromising key third-party service providers or embedded software components, threat actors can strategically turn a company’s own partners and IT infrastructure into gateways for initial access or to put pressure on suppliers.
67% of organizations that experienced a ransomware attack in the past three years said their attackers contacted customers and/or partners about the breach to force payment.
“We found that 52% of global organizations have had a supply chain organization hit by ransomware, potentially putting their own systems at risk of compromise. But many aren’t taking steps to improve partner cybersecurity. The first step towards mitigating these risks must be enhanced visibility into and control over the expanding digital attack surface.”
– Bharat Mistry, Technical Director at Trend Micro
The MOVEit vulnerability, a critical zero-day identified as CVE-2023-34362, is an example of how ransomware can exploit supply chain weaknesses.
This vulnerability, affecting the MOVEit file transfer tool, allows attackers to access and manipulate the MOVEit database.
Exploited extensively by the CL0P ransomware group, this flaw enabled the attackers to upload a web shell and exfiltrate sensitive data, effectively compromising the security of the organizations relying on this transfer tool.
The MOVEit incident, initially reported on May 31, 2023, quickly escalated as the CL0P group publicly claimed responsibility for the attack, threatening to send ransom demands to impacted companies starting June 14.
So far over 2,600 organizations across finance, healthcare, and education have fallen victim to this attack. It’s estimated that the total cost of this attack has reached $10B.

5. Infected USB Drives
Infected USB drives and other removable media are a simple yet effective tactic to spread ransomware.
In the first half of 2023, Mandiant Managed Defense saw a threefold increase in the number of attacks using infected USB drives.
The problem arises when malware infected USBs or devices are plugged into an unsecured network connected device.
The moment they are connected, the malware can be executed and the encryption process can begin.
The impact can be devastating with 79% of USB-based security threats causing widespread disruption to critical business operations and destruction to operational technology.
The nature of this attack lies in its exploitation of human curiosity and trust in physical objects.
These devices, often shared among colleagues and friends or found and used out of curiosity, serve as Trojan horses, breaching secured networks and bypassing conventional defenses.
According to Honeywell’s 2022 Industrial Cybersecurity USB Threat Report, 52% of malware in 2022 was designed to exploit USB or propagate over USB.
Threat actors will also deliberately leave infected USB drives in public places or distribute them to unsuspecting users.
In some cases, they may even deliver USBs directly to the organization with the hope that an employee will use them.
Protecting Your Business From Ransomware Attacks
A few practical ways to protect your business from ransomware attacks include:
- Provide Security Awareness Training – Give employees continuous security training to equip them with the knowledge to detect and respond to threats, reducing risk from 60% to 10% in the first 12 months.
- Implement 3 Factor Authentication – Add an extra layer of security with 3 factors – something you know, something you have, and something you are – to prevent 99.9% of password compromises.
- Microsegment Devices And Users – Break the network into isolated segments with restricted access to limit ransomware’s ability to spread throughout the system.
- Develop A Ransomware Response Plan – Create a plan outlining immediate steps to isolate infections and restore systems to minimize disruption from an attack.
- Keep Systems Up To Date – Adopt daily scanning and patching of vulnerabilities to significantly reduce the window of opportunity for exploitation.
- Regularly Back Up Data – Use a multifaceted backup strategy across cloud, physical, local, and offsite formats to ensure malware-free recovery options.
- Have A Disaster Recovery Plan – Define downtime tolerance, recovery procedures, and comprehensive testing strategies to mitigate ransomware impacts.
- Perform Red Team Or Table Top Exercises – Test incident response plans and leadership reactions to identify security gaps and improve readiness.
- Work With A Virtual CISO – Collaborate with an experienced advisor to design response plans and enable data-driven security decisions.
- Use Strong Password Policies And Management Tools – Enforce complex passwords, frequent rotation, and centralized control to prevent unauthorized access.
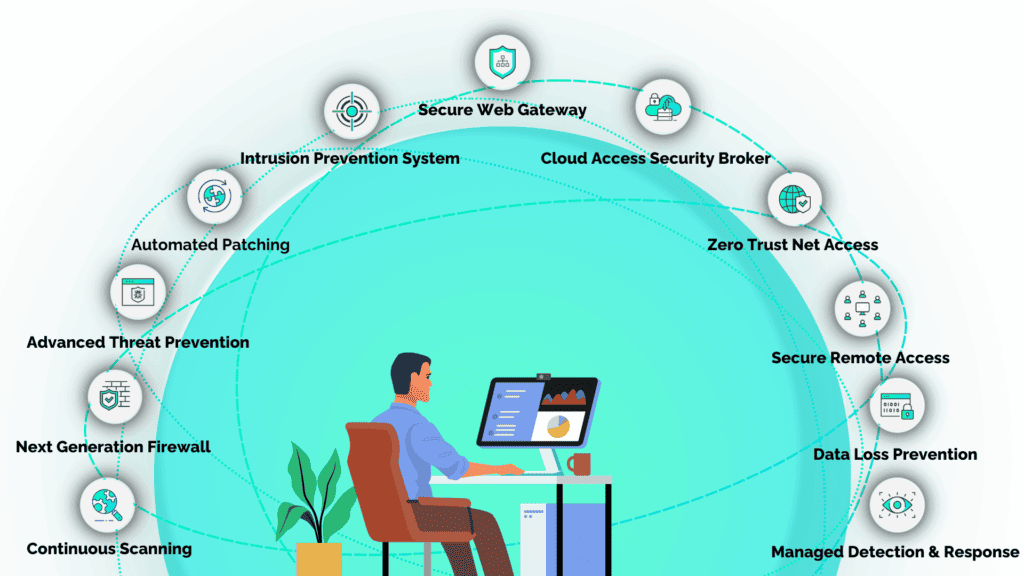
How SecureTrust Stops Ransomware
SecureTrust addresses ransomware protection and prevention for small businesses through an affordable subscription-based model.
Implementation is easy with a 10 minute setup designed to get you back to work while seamlessly protecting your organization 24/7.
These services are fully managed by DoD trained experts who work with your business to monitor, detect, respond, and proactively hunt for threats on your network.
Extended Threat
Protection (XTP)
Monthly subscription
(per device)
*All prices listed are in US Dollars. Subscription will automatically renew for 1 month from the date of purchase unless you cancel.
Helios Cloud™
Enterprise Security
Monthly subscription
(per device)
*All prices listed are in US Dollars. Subscription will automatically renew for 1 month from the date of purchase unless you cancel.
Extended Threat Protection (XTP) provides 3 factor authentication proven to reduce credential threat risk by 99.9% while reducing IT support tickets by 75% by simplifying password policies.
This solution also includes microsegementation that leverages Secure Access Service Edge (SASE) technologies delivered through Helios Cloud™ to provide comprehensive network security.
Finally, a continuous approach to vulnerability management ensures all network connected devices, whether onsite or remote, are up to date with the latest security patches.
With SecureTrust, small businesses can confidently navigate the complex landscape of cybersecurity, ensuring your data and operations are safeguarded against the growing threat of ransomware.
Frequently Asked Questions
Why Is Ransomware So Effective?
Automation, AI, and the rise of Ransomware as a Service (RaaS) have made ransomware one of the most effective and accessible forms of cyber attack. This is due to its low cost to operate and a high return on investment.
Ransomware gangs are searching for the lowest-hanging fruit. Unpatched systems with critical/high exploitable vulnerabilities or insider threats (malicious or unintentional) require little investment from threat actors to gain access.
Unfortunately, small and medium-sized businesses that often lack mature security programs or internal expertise make for the perfect targets.
Once ransomware has spread companies are typically forced to make one of two decisions:
- Pay the ransom, which means you will likely become a victim of a future extortion attempt.
- Lose access data to be sold on the black market to a competitor if it’s IP, or for future cyber attacks if the data is personal or medical information.
How Does A Ransomware Attack Happen?
A ransomware attack happens when malicious code, or malware, is installed either by a user or the threat actor themselves.
To gain access to a network or device, threat actors must first trick the user into providing credentials (username/password) or get the user to download the malware on a network connected device.
Once the threat actor has initial access they will look for ways to escalate their privileges to a domain admin.
If successful, they can lock other admins out by resetting the password and multi factor authentication settings.
Finally, the attacker will begin to encrypt your data.
It’s important to note that the encryption process can take minutes to complete.
The mean time for encrypting 100,000 files is 6 minutes, with the longest taking around 45 minutes.
How Does A Computer Or Device Become infected With Ransomware?
A computer or device can become infected with ransomware through several methods including:
- Getting users to visit a malicious website.
- Tricking users into downloading malware.
- Socially engineering an employee.
- Bypassing multi factor authentication
- Using remote desktop protocol.
- Targeting victims using public WiFi.
- Targeting victims using public charging ports.
- Installing malware on portable devices e.g. USB drives.
What Are The Signs Of A Ransomware Attack?
The typical signs of a ransomware attack include:
- Sudden inaccessibility of files, with common document types often replaced by unfamiliar extensions.
- Users frequently encounter ransom notes on their screens.
- System performance may deteriorate, as ransomware consumes significant processing resources.
- Unusual network communications, often a sign of data being exfiltrated or encryption keys being exchanged with the attacker’s server.
What Should I Do If My System Has Been infected By Ransomware?
If you’re experiencing a ransomware attack, then you should:
- Document all details of the attack for future reference and investigation.
- Immediately disconnect the infected device from the internet and other network connections to prevent the spread.
- Check for backups to restore your data; if unavailable, consider tools provided by cybersecurity communities for decryption.
- Avoid paying the ransom, as it doesn’t guarantee file recovery and may encourage further attacks.
- Contact a cybersecurity professional for assistance.
- Report the incident to relevant authorities to help combat cybercrime.
- Category: Ransomware










